The last use case for localized data policies that we are going to examine in this section is how to configure a mirror instance that sends a copy of certain data traffic to a specified destination for analysis, as shown in figure 1 below.
The configuration process consists of two steps.
- First, we define the mirror instance by giving it a user-defined name.
- Then under the instance, we specify the remote-destination address that will receive the copy of the data and the router’s source address that will be used.
In our example, the mirror packet will be sourced from vEdge-5's Ge0/5 interface that has an IP address of 10.5.5.1 and the remote destination would be 10.6.5.4. Therefore, the mirror instance will have the following configuration:
policy
mirror MIRROR-1
remote-dest 10.6.5.4 source 10.5.5.1
!
After we configure the mirror instance, we invoke it in an ACL sequence as shown in the output below:
policy
access-list ACL-VPN5
sequence 11
match
source-ip 10.5.5.4/32
destination-ip 10.1.5.1/32
protocol 1
!
action accept
mirror MIRROR-1
!
default-action accept
!
The last step is to apply the ACL under an interface. In our example, we are going to configure the access list under vEdge-5’s Ge0/5 interface.
vEdge-5# conf t
Entering configuration mode terminal
vEdge-5(config)# vpn 5 int ge0/5
vEdge-5(config-interface-ge0/5)# access-list ACL-VPN5 in
vEdge-5(config-interface-ge0/5)# commit
Commit complete.
Once the ACL is applied, we can ping from 10.1.5.1 to 10.5.5.4 and make a Wireshark capture to see what the copied traffic looks like:
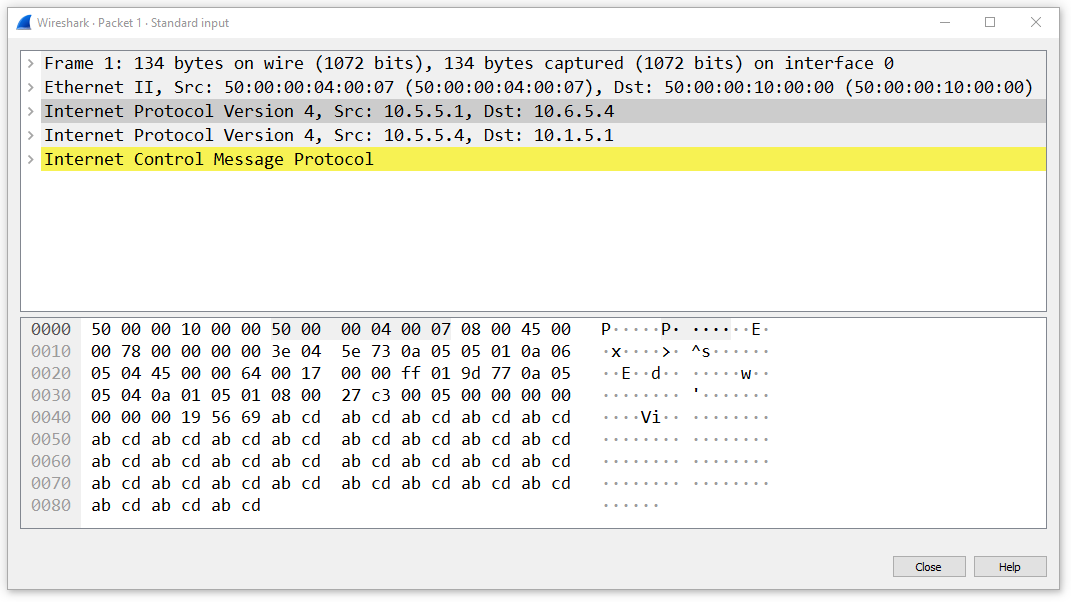
Notice that the copied packet has an additional outer IP header with the source/destination IP addresses configured in the mirror instance. Also, notice that the traffic is encapsulated neither with GRE nor with IPsec. This means that the copied traffic is sent through the underlay using the VPN0’s routing table.
Mirroring Traffic: Key Takeaways
- Configuring traffic mirroring on a vEdge device is a two-step process:
- First, we configure the mirror instance;
- Then, we invoke the mirror instance in a match-action rule of an access list.
- The mirrored traffic is encapsulated with a new IP header. Source and destination IP addresses are taken from the mirror instance configuration.
- The mirrored traffic is sent using VPN0’s routing table on the underlay network.